Ever encountered the cryptic message “Remote Host Key Has Changed” while connecting to a server using SSH (Secure Shell)?
This seemingly technical error notification actually serves as a vital security safeguard.
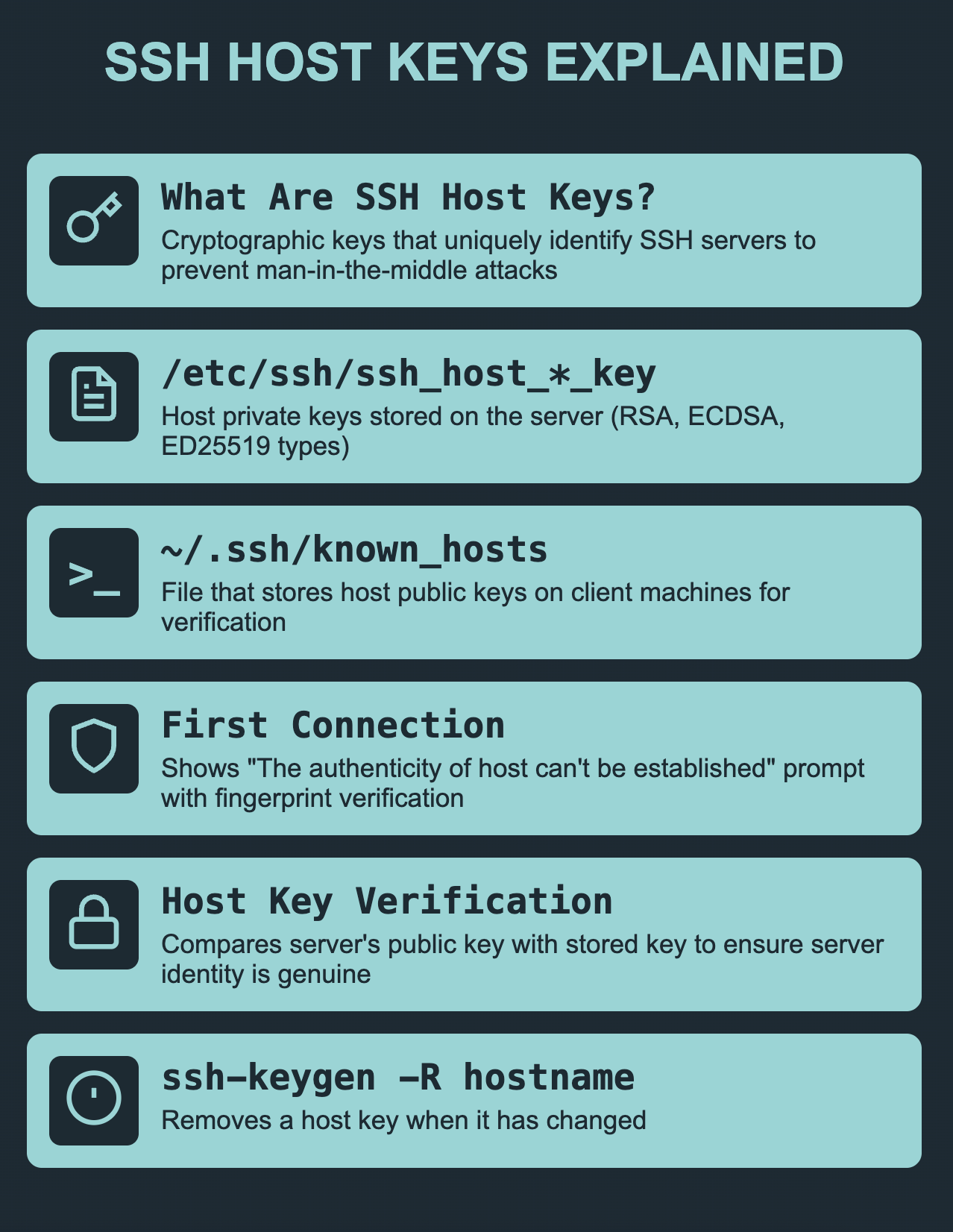
Each server in the SSH world has a one-of-a-kind identifier called a host key, similar to a digital fingerprint.
When you connect for the first time, the server sends its unique key to your device. Your device stores this key in a file named “known_hosts“.
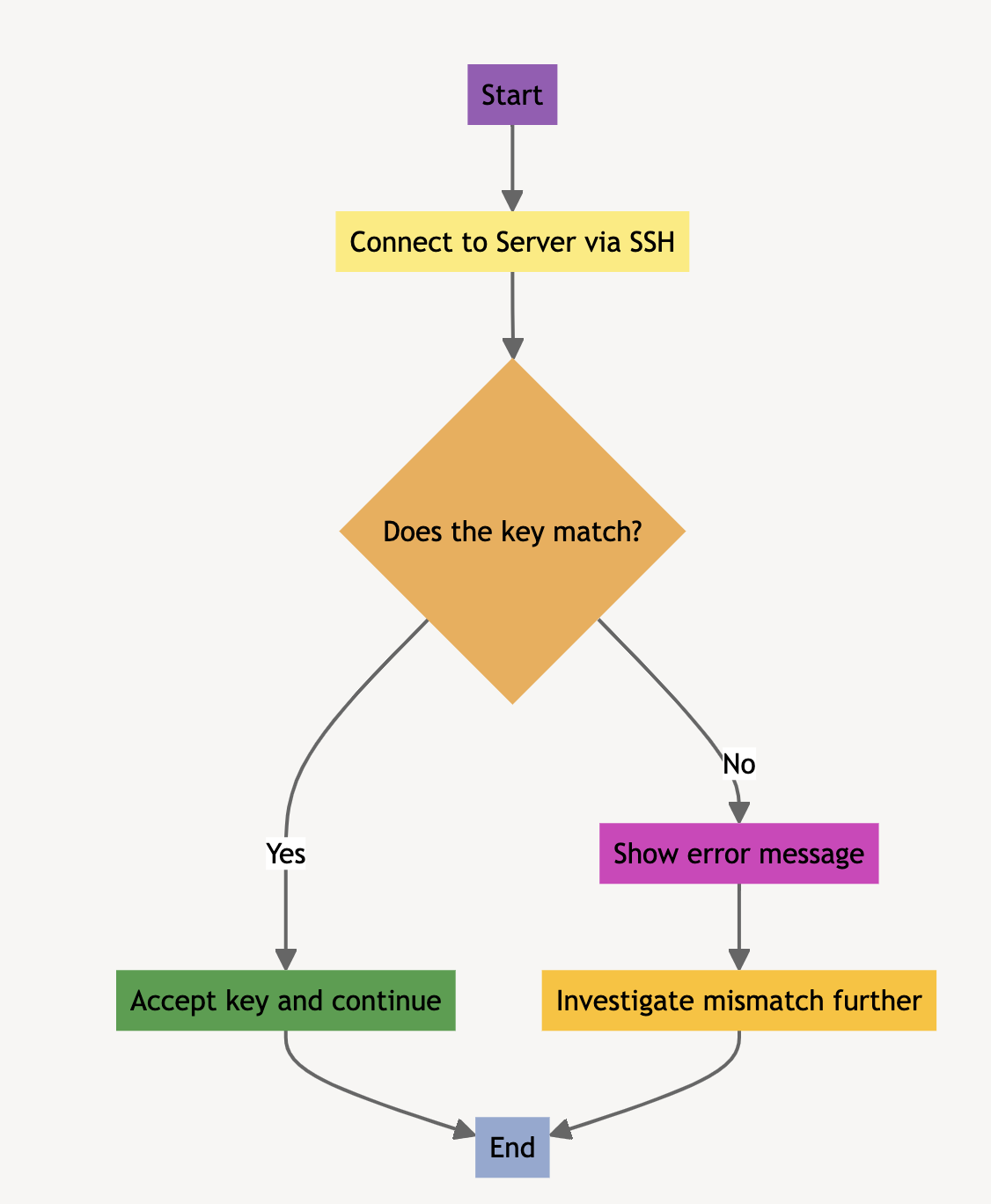
On subsequent connections, the server again sends its key. Your device checks this key against the one stored in “known_hosts”. If they match, you’re good to go – the connection is secure.
A mismatch between the keys triggers the warning.
This prevents someone from intercepting your connection and pretending to be the real server.
By checking the key, you ensure you’re actually communicating with the intended server.
This video shares more about SSH host key.
See also: Mastering the Linux Command Line — Your Complete Free Training Guide
Table of Contents
What is host key in Linux
An SSH host key is another layer of security used in the SSH protocol, specifically on the server side. It works alongside SSH key pairs (private and public keys).
The main purpose of an SSH host key is to ensure you’re connecting to the intended server and not a malicious imposter in a process called server authentication. It acts as an extra layer of security on top of username and password logins.
Here’s how it works:
- Unique Server Identity: Every server has a unique SSH host key, similar to a digital fingerprint. It consists of a public and private key pair, just like user SSH keys, but these keys are stored on the server itself.
- Verification on Connection: When you connect to a server for the first time using SSH, the server sends its public host key to your local machine.
- Matching Keys: Your SSH client (the program you use to connect) checks its stored list of known host keys. This list can include keys for servers you’ve connected to before or pre-configured trusted keys.
- Security Alert:
Match: If the public host key from the server matches a known host key in your list, it’s considered a secure connection.
Mismatch: If the keys don’t match, it could be a red flag:
You might be trying to connect to a different server than intended (posing as a legitimate server).
The server’s key might have been changed due to os rebuild.
Remote Host Key Has Changed Error: Explanation and Fix
We can summarize what we have explained above.
- SSH Host Keys: Every server has a unique SSH host key, acting like a digital fingerprint for identification.
- Known Hosts File: Your SSH client maintains a file called “known_hosts” that stores previously encountered server keys.
- The Check: When you connect to a server, the server sends its host key to your client.
- The Mismatch: The client checks the “known_hosts” file for a matching key. If it doesn’t find a match, or if the keys differ, you get the error message.
The “Remote Host Key Has Changed” error in SSH indicates a mismatch between the current server’s host key and the one previously recorded in the client’s known_hosts file.
This discrepancy can occur due to legitimate reasons like a reinstalled operating system or an updated SSH server package. However, it may also signal a potential security threat, such as a man-in-the-middle attack.
How you respond to this error message depends on the situation. If you’re confident about the server’s legitimacy and the key change was expected, you can take steps to accept the new key.
However, if you’re unsure, it’s always best to err on the side of caution and investigate further before proceeding. This might involve contacting the server administrator to confirm the key change or double-checking the server’s identity through a trusted channel.
How to Fix:
- Verify the Change: Confirm the legitimacy of the change in the host key. Investigate further if there’s any doubt about the change’s authenticity.
- Remove the Old Host Key: Use the command ssh-keygen -R [hostname_or_IP] to remove the old key from the known_hosts file.
- Reconnect to the Server: After removing the old key, reconnect with the command ssh [username]@[hostname_or_IP]. You will be prompted to accept the new host key, which should be carefully verified before acceptance.
- Key Re-Added: Once the new key is accepted, it is added to the known_hosts file, securing future connections to the server.
How to Find the Host Key in Linux
Understanding how to locate the host key of an SSH server in Linux is important for verifying the server’s identity and for troubleshooting purposes.
Finding the Local SSH Server’s Host Key
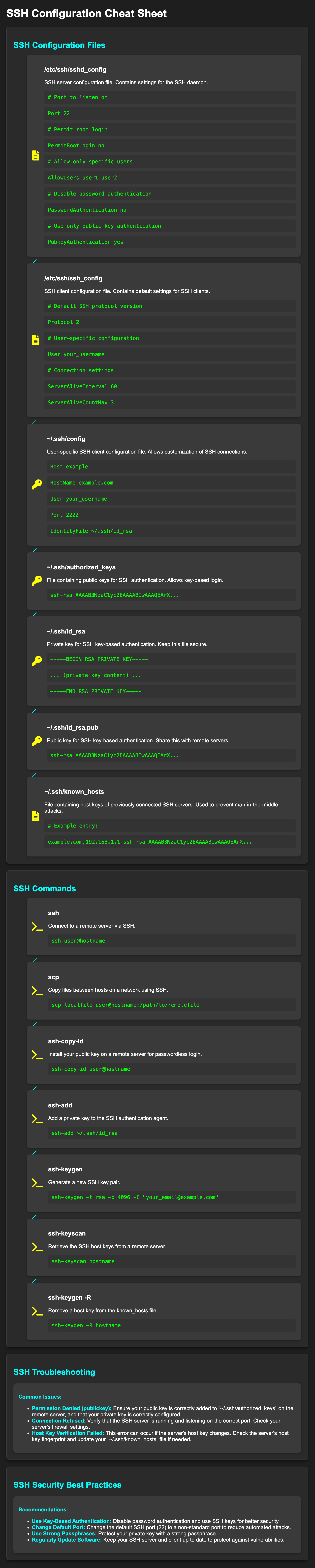
- Access the SSH Server’s Host Key Files: SSH host keys are typically stored in /etc/ssh/. File names vary based on the key type (e.g., ssh_host_rsa_key.pub, ssh_host_ecdsa_key.pub).
- View the Host Key: Use the cat command to display the public part of the host key, for example:
cat /etc/ssh/ssh_host_rsa_key.pub
Finding a Remote SSH Server’s Host Key
This method allows you to retrieve the public host key of a server without needing to have connected to it before. Here’s how to use it:
- Open a terminal window.
- Run the ssh-keyscan command:
ssh-keyscan <server_ip_or_ hostname
Replace with the actual IP address or hostname of the server you want to find the key for. - Output: The command will display the public host key of the server along with the SSH protocol version and any key fingerprints (hashed versions of the key for easier comparison).
Get the server’s public host keys (unauthenticated)
# show RSA/ED25519/ECDSA keys (unauthenticated)
ssh-keyscan -t rsa,ecdsa,ed25519 example.com
# hash hostnames when adding to known_hosts
ssh-keyscan -H example.com
# fetch a server on a non-standard port
ssh-keyscan -p 2222 example.com
ssh-keyscan contacts the SSH server and prints its public host keys. NOTE: this is not authenticated—an attacker who intercepts your connection could return bogus keys.
2) Show fingerprint(s) from the output
Pipe the key(s) into ssh-keygen to display human-readable fingerprints (SHA256 or MD5 depending on your ssh-keygen version):
ssh-keyscan example.com | ssh-keygen -lf -
This prints something like:
2048 SHA256:AbCdEf... (RSA)
256 SHA256:ZyXwVu... (ED25519)
(Using -lf - tells ssh-keygen to read the public key from stdin.)
3) Add the server key to your ~/.ssh/known_hosts (if you trust it)
ssh-keyscan -H example.com >> ~/.ssh/known_hosts
Hhashes the hostname inknown_hosts. Don’t blindly add keys unless you’ve verified them.
4) Inspect known_hosts entries
# find entries for host
ssh-keygen -F example.com
# show fingerprint for a specific known_hosts line
ssh-keygen -lf ~/.ssh/known_hosts
5) Check host key directly on the server (requires server access)
On the server itself:
# For the public host key files (typical paths):
sudo ssh-keygen -lf /etc/ssh/ssh_host_rsa_key.pub
sudo ssh-keygen -lf /etc/ssh/ssh_host_ecdsa_key.pub
sudo ssh-keygen -lf /etc/ssh/ssh_host_ed25519_key.pub
This is the most reliable way: read the host’s public key directly from /etc/ssh.
Conclusion
Resolving the “Remote Host Key Has Changed” error involves verifying the cause of the key change, removing the outdated key, and updating the known_hosts file with the new key.
This process is essential for maintaining the integrity and security of SSH connections.
It’s important to prioritize security when dealing with SSH host keys. Don’t blindly accept new keys, especially if you’re unsure about the server. Always verify the server’s identity before adding new keys to your “known_hosts” file.
Fix SSH timed out waiting for input: auto-logout with TMOUT and StopIdleSessionSec Configurations
Obtaining SSH Host Key Fingerprint in Linux
15 SSH Best Practices Every Linux Admin Should Know
5 ways to fix ssh: connect to host port 22: Connection refused




[…] SSH Host key and How to Fix Remote Host Key Has Changed Error […]