The ssh known_hosts file is a file that stores the public key of all of the servers that you have connected using ssh.
This file is used to verify the identity of servers in the future. Ssh can automatically add keys to this file, but they can be added manually as well.
In this article, I will share everything about the SSH know_hosts file.
Table of Contents
What is SSH known_hosts file?
In the context of computer networking, known_hosts is a file used by SSH (Secure Shell) clients to verify the identity of a remote server before establishing a connection.
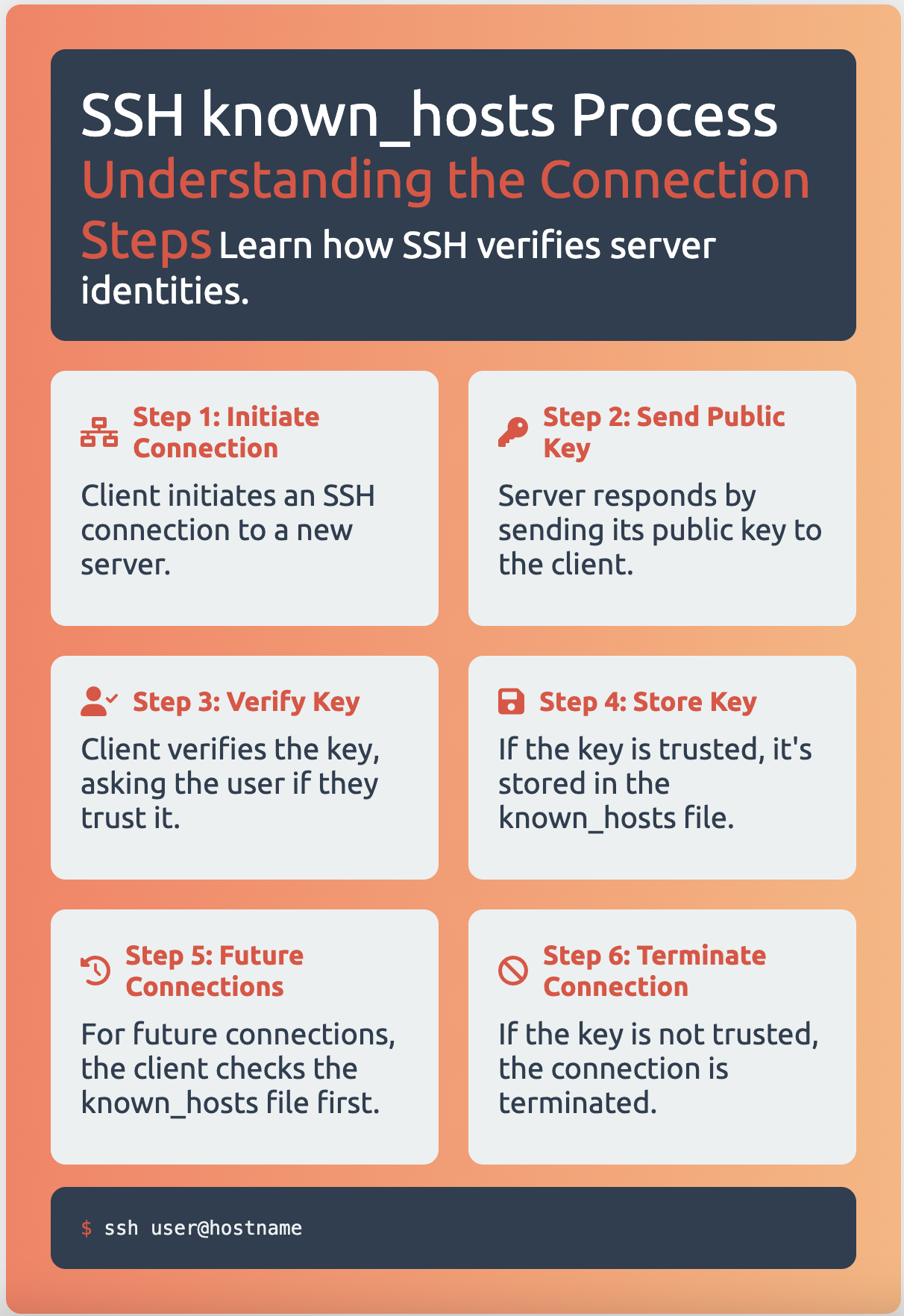
When an SSH client connects to a server for the first time, the server’s public key is exchanged with the client and saved in the known_hosts file on the client’s system.
On subsequent connections, the client verifies the server’s identity by checking the key in the known_hosts file against the one presented by the server.
If there is a match, the connection will proceed. If the match fails, ssh will fail with an error message.
If there is no key at all listed for that remote host, then the key’s fingerprint will be displayed and there will be the option to automatically add the key to the file.
This file can be created and edited manually, but if it does not exist it will be created automatically by ssh when it first connects to a remote host.
The known host file is stored in /etc/ssh/known_hosts or in .ssh/known_hosts in each user’s home directory.
See also: Mastering the Linux Command Line — Your Complete Free Training Guide
Format of known_hosts file in SSH
The format is one public key or certificate per unbroken line.
Each line contains a hostname, number of bits, exponent, and modulus. At the beginning of the line is either the hostname.
It is possible to use a comma-separated list of hosts in the hostname field if a host has multiple names or if the same key is used on multiple machines in a server pool.
SSH known_hosts Example
Here is one example of host key with IP:
10.254.171.53 ecdsa-sha2-nistp256 AAAAE2VjZHNhLXNoYTItb
POVVQF/CzuAeQNv4fZVf2pLxpGHle15zkpxOosckequUDxoq
SSH known_hosts file permissions
- $HOME/.ssh folder should have permission 700.
- config and private/secret key files id_rsa_XXX should have 600.
- known_hosts and public/shared key files id_rsa_XXX.public should have 644.
Add public key to known_hosts manually
We can use ssh-keygen with -F option to search known_hosts file.
$ ssh-keygen -F server3.example.com
The default file to be searched will be ~/.ssh/known_hosts and the key is printed if found. A different file can be searched using the -f option.
If a key must be removed from the file, the -R option works similarly to search by host and then remove it.
$ ssh-keygen -R server4.example.com -f ~/.ssh/known_hosts
When a key is removed, it will then be appended to the file ~/.ssh/known_hosts.old in case it is needed later.
How to view the ssh known_hosts file?
To view the ssh know_hosts file on your Linux system, you can use the following command:
cat ~/.ssh/known_hosts
or
vi ~/.ssh/known_hosts
To add a new host to the ssh know_hosts file, you can use the following command:
$ ssh-keyscan -t rsa [remote.server.com] >> ~/.ssh/known_hosts
$ ssh-keyscan -H remote.server.com >> ~/.ssh/known_hosts
To remove a host from the know hosts file, you can use the following command:
$ ssh-keygen -R [remote.server.com]
$ ssh-keygen -r [remote.server.com]
Where should I store my ssh known_hosts file?
The ssh known_hosts file should be stored in the ~/.ssh directory.
For example, the full path to the ssh know_hosts file is: ~/.ssh/known_hosts
What are some common problems with the ssh known_hosts file?
The ssh know_hosts file is a file that stores information about hosts that you have connected to using ssh. This file can help to prevent man-in-the-middle attacks by verifying the host key before connecting.
A common problem with the ssh know_hosts file is when you try to connect to a host and get an error message: “WARNING: REMOTE HOST IDENTIFICATION HAS CHANGED!”
This usually happens if you changed out hardware on the server that you are connecting to, or if there was some other change in settings on the remote server.
If you get this error message, you can fix it by removing the host from your ssh know_hosts file and adding it back again:
$ ssh-keygen -R [remote.server.com]
$ ssh-keyscan -t rsa [remote.server.com] >> ~/.ssh/known_hosts
$ ssh-keyscan -H remote.server.com >> ~/.ssh/known_hosts
Another common problem with the ssh know_hosts file is when you try to connect to a host and get an error message: “WARNING: POSSIBLE DNS SPOOFING DETECTED!” .
This usually happens when you try to connect to a host that does not exist.
If you get this error message, then check your /etc/hosts file and make sure that the name of the remote server is there and it has a valid IP address assigned to it.





[…] to an SSH server for the first time, the server’s host key is stored in the client’s known_hosts […]