The SSH authorized_keys file is a file that contains a list of public keys that are authorized to log in to the server. This file is used to prevent unauthorized users from connecting to the SSH server.
The primary purpose of this guide is to illustrate the use of the ~/.ssh/authorized_keys file.
After reading this article, we will know how ssh authentication works, what the ssh authorized_keys file is.
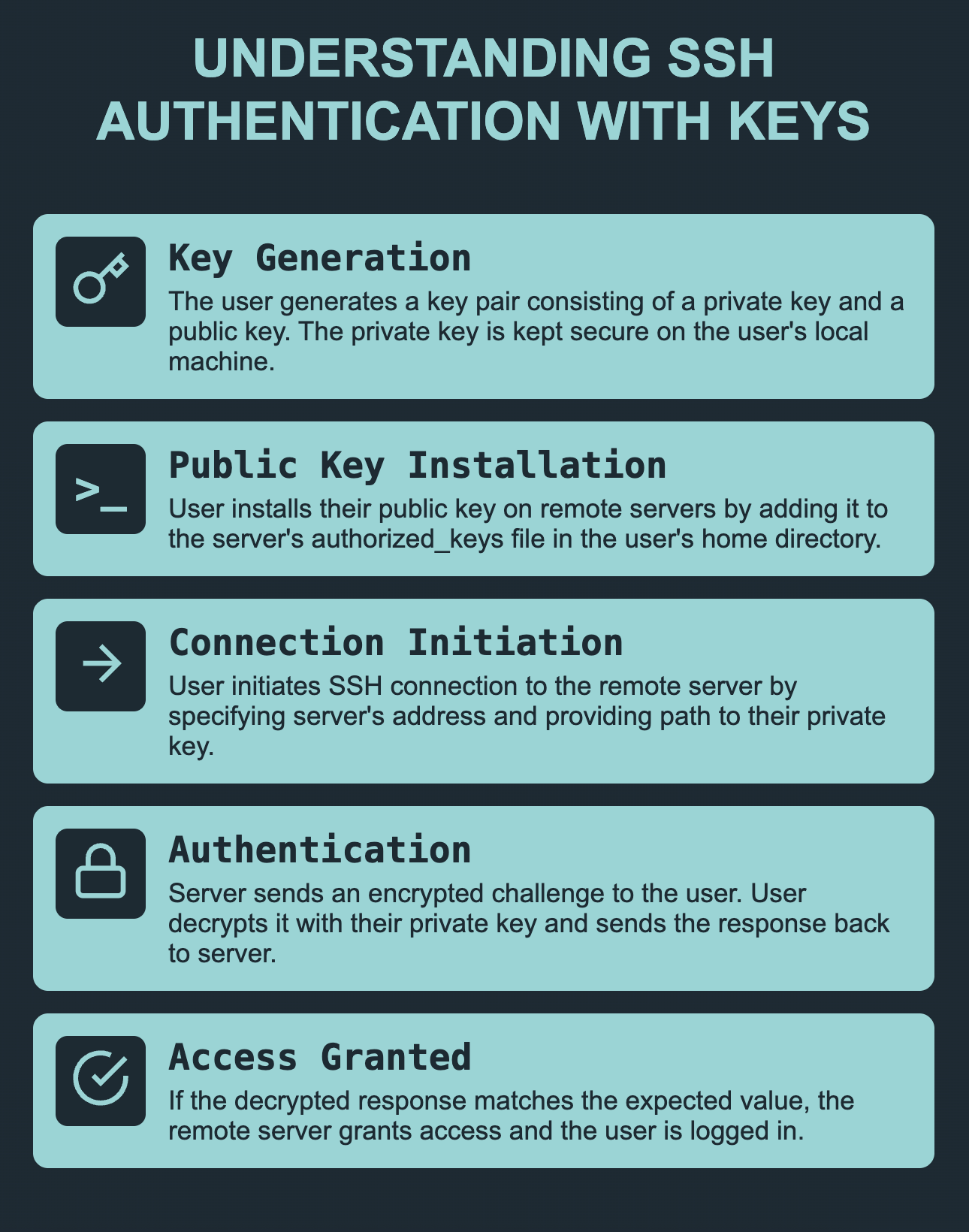
Table of Contents
Understanding SSH Authentication with Keys
- Key Generation: The user generates a key pair consisting of a private key and a public key. The private key is kept on the user’s local machine and is used for authentication. The public key is shared with remote servers and is used to verify the user’s identity.
- Public Key Installation: The user installs their public key on the remote server(s) they wish to log into by adding it to the server’s authorized_keys file. This file is usually located in the user’s home directory on the remote server.
- Connection Initiation: The user initiates an SSH connection to the remote server by specifying the server’s IP address or hostname and providing the path to their private key.
- Authentication: Upon receiving the connection request, the remote server sends a challenge to the user. The challenge is encrypted using the user’s public key. The user decrypts the challenge using their private key and sends the decrypted response back to the server.
- Access Granted: If the decrypted response matches the expected value, the remote server grants access to the user and the user is logged in.
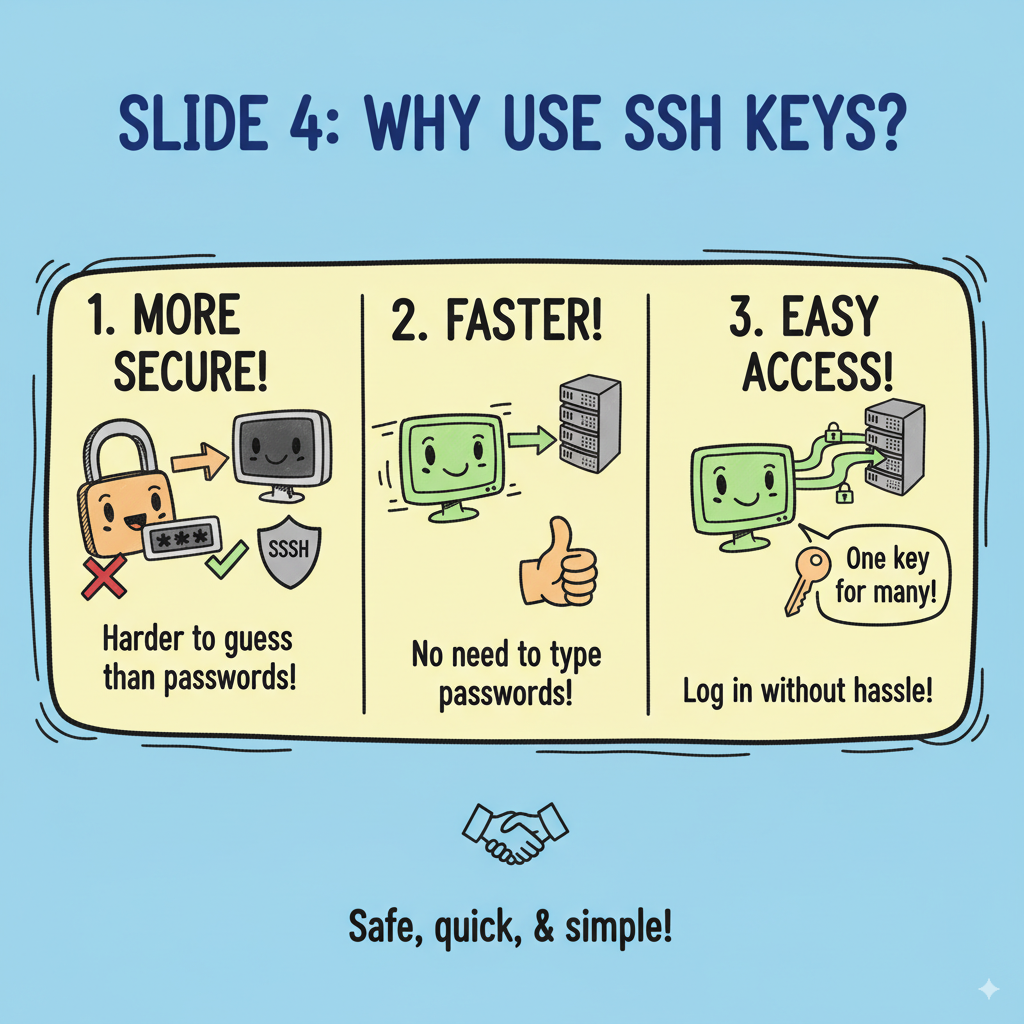
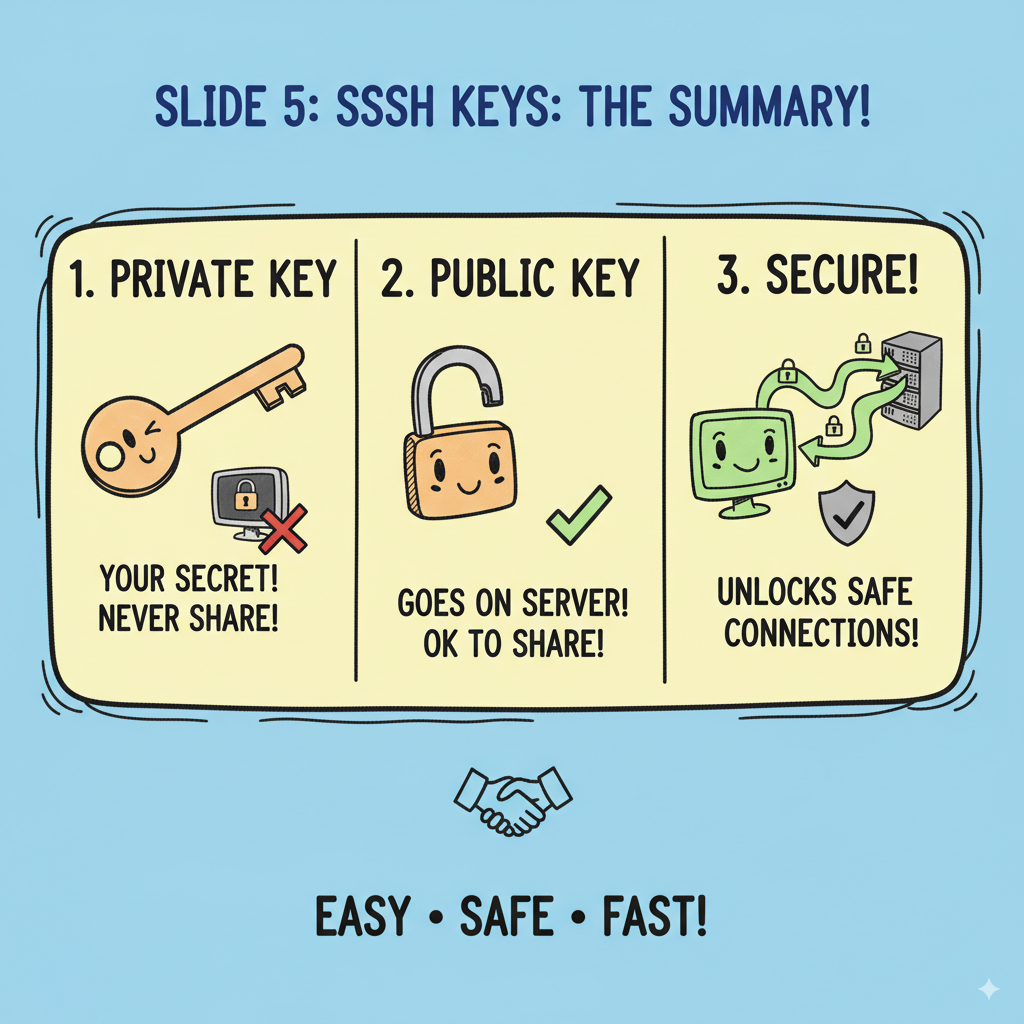
You can check out this helpful guide to get the detailed steps on how to use SSH Keys.
Understanding SSH authorized_keys
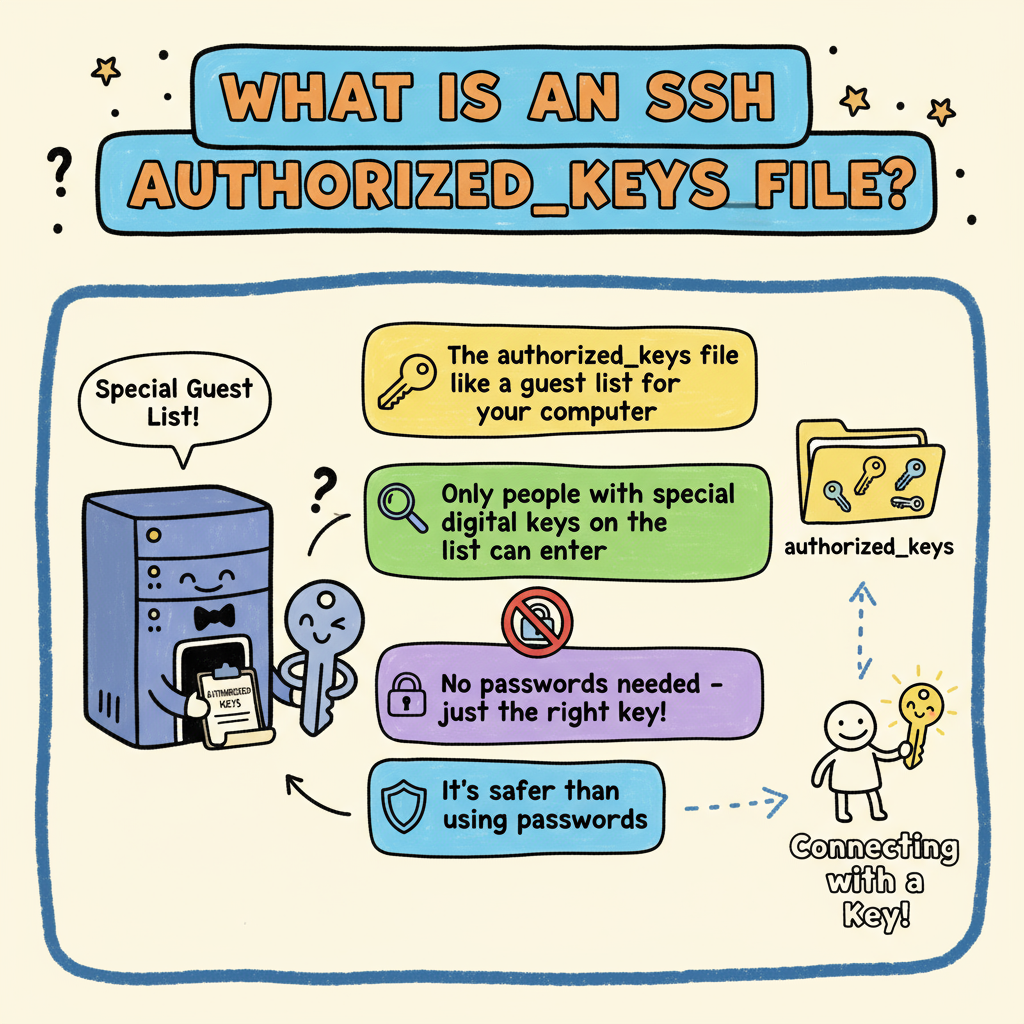
The ssh protocol has 2 sides: the client and the server. The SSH key-based authentication uses ssh keys to verify that the user is authorized.
If the ssh key is correct, it allows user to login without asking username or password.
let’s get into the details.
SSH authorized_keys is a file located in the user’s home directory on a remote server that is used to specify public keys that are authorized for logging in to the user’s account.
See also: Mastering the Linux Command Line — Your Complete Free Training Guide
When a user attempts to log in to a remote server using SSH key-based authentication, the server checks the user’s public key against the authorized_keys file to verify that the user is authorized to access the server.
Authorized_keys files can be edited manually to add or remove keys, but it’s recommended to use the ssh-copy-id command to add a user’s public key to the file.
This command copies the public key to the remote server’s authorized_keys file while preserving any existing keys, and sets the correct permissions on the file to ensure that it can be used for SSH key-based authentication.
The authorized_keys file plays a critical role in this process by storing the public keys that are authorized to access the remote server.
By managing the authorized_keys file, administrators can control who has access to the server. They can also revoke access to the server by removing a user’s public key from the file.
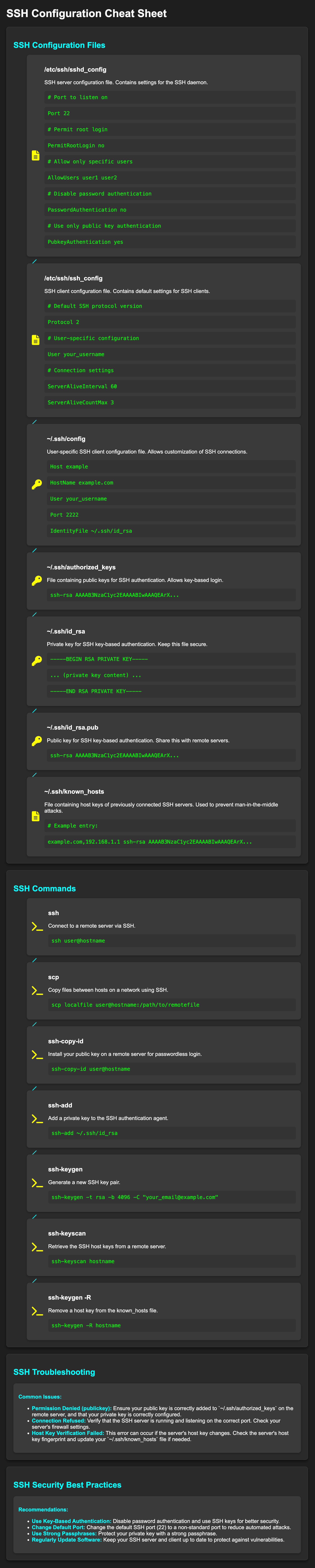
Format of SSH authorized_keys file
To view the content of the authorized_keys file, you can use a text editor or a command-line tool like cat or less.
Here’s how to do it using the cat command:
Open a terminal window.
Navigate to the .ssh directory using the following command:
cd ~/.ssh
Type the following command to view the content of the authorized_keys file:
cat authorized_keys
This will display the content of the file in the terminal.
Alternatively, you can use the less command to view the content of the file.
The less command allows you to navigate through the content of the file using the arrow keys.
The authorized_keys file contains SSH public key.
The format of each line is as follows:
ssh-[type] [public key] [comment]
Here’s a breakdown of each part of the format:
ssh-[type]: This specifies the type of the public key. The most common type is ssh-rsa, which is based on the RSA algorithm. Other types include ssh-dsa, which is based on the Digital Signature Algorithm (DSA), and ssh-ed25519, which is based on the Ed25519 algorithm.
[public key]: This is the actual public key, which is a long string of characters.
[comment]: This is an optional comment that can be added to the end of the line. It can be used to identify the key, such as with the user’s name or the machine name.
An example for user bob is the following:
ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABAQDJlG20rYTk4o
k+xFjkPHYp/R0LfJqEYDLXA5AJ49w3DvAWLrUg+1CpNq76WS
qmQBmoG9jgbcAB5ABGdswdeMQZHilJcu29iJ3OKKv6SlCulAj1t
HymwtbdhPuipd2wIDAQAB
File permission of SSH authorized_keys file
The ssh authorized_keys file should be placed in a directory which is only accessible by the user. For example, the ~/.ssh directory.
ssh authorized_keys file permissions should be set to 600 which means that only the user who owns the file can read and write to it.
You can check out this helpful guide on checking file permissions in Linux. It provides a clear and concise explanation of how to use the ls command to view file permissions and access modes, and also covers how to modify file permissions using the chmod command.
Here’s an example of the ls command output for the authorized_keys file with the recommended permissions:
-rw------- 1 user user 400 May 6 10:15 authorized_keys
The directory ~/.ssh/ should have permissions set to 700, which means that only the owner of the directory (the user) can read, write, or access it.
where is the SSH authorized_keys file located?
The authorized_keys file is located in the .ssh directory. This directory is located in the user’s home directory.
The filename for the authorized_keys file is typically authorized_keys.
So, the full absolute file path for the authorized_keys file for a user named username on a remote server is:
/home/username/.ssh/authorized_keys
How to add keys to SSH authorized_keys file?
- Generate a public-private key pair on your local machine using the ssh-keygen command.
This will create two files: a public key file (usually named id_rsa.pub) and a private key file (usually named id_rsa).
- Copy the public key to the remote server using the ssh-copy-id command.
This command will automatically add the public key to the authorized_keys file on the remote server and set the correct permissions.
Here’s an example:
ssh-copy-id user@remote_server
This command will prompt you for the remote server user’s password. After entering the password, the public key will be copied to the remote server.
If the ssh-copy-id command is not available on your local machine, you can manually copy the public key to the remote server using a text editor or the scp command.
How to Verify that the public key was added to the authorized_keys file on the remote server?
You can view the contents of the authorized_keys file using the cat command:
cat ~/.ssh/authorized_keys
This command will display the contents of the authorized_keys file. If the public key was added correctly, it should be listed at the end of the file.
That’s it! You can now use the private key to log in to the remote server without entering a password each time.
The SSH client on your local machine will automatically use the private key to authenticate with the remote server.
FAQ about SSH authorized_keys file
What is the best way to enable SSH login without password?
The best way to enable SSH login without password is to use an SSH key. SSH keys are more secure than passwords, and they can be used to authenticate with multiple accounts on different systems.
You can use the ssh-keygen command to generate an SSH key. For example, if you want to generate an RSA key, you would type:
ssh-keygen -t rsa
Why is the ssh public key not working for me when trying to log in?
There could be a number of reasons why your ssh public key is not working. Make sure that you are using the correct key, and that the key has been added to the authorized_keys file on the server.
How do I troubleshoot issues with the authorized_keys file?
A: If you are having issues with the authorized_keys file, you can check the file permissions, file location, and file content. You can also check the SSH server logs for error messages.



